CYBERSECURITY
Full Protection
Cybersecurity can be cost-efficient!

Unique Mix of OT & IT Cybersecurity for Every Business Sector

Basic Tier: suits small companies
- Digital Inventory Check
- Security Assessments
- Vulnerability management
- Cybersecurity Training
- Emergencies

Standard Tier: better for SME
- IT Infrastructure Compliance Audit
- 24/7 monitoring and threat detection
- Incident response, Forensic & Recovery
- Cybersecurity Training
- Costs Cut

Advanced Tier: for any Corporate need
- IT Asset Inventory Compliance (ISO 27001/NIST)
- 24/7 SOC deployment / Red Teaming
- Strategic Guidance
- Training & Knowlage sharing
- Significant Costs Cut
CUSTOMIZATION OPTIONS
INDUSTRY-SPECIFIC MODULES
ADVANCED AI THREAT HUNTING
THREAT CONTAINMENT AND ERADICATION
CUSTOM INCIDENT RESPONSE AND DFIR SERVICES
CUSTOM TRAINING AND WORKSHOPS
WEB AND EMAIL SECURITY SERVICES
DATA LEAKAGE PREVENTION SERVICES
IDENTITY AND ACCESS SOLUTIONS
AI FORWARD DETECTION SOLUTIONS AND SERVICES
REGULATORY COMPLIANCE AND BEST PRACTICES ADVISORY
EXECUTIVE CYBERSECURITY BRIEFINGS
VULNERABILITY ASSESSMENTS AND PENETRATION TESTING
CLOUD SECURITY MANAGEMENT
SECURITY ARCHITECTURE REVIEW AND OPTIMIZATION
INCIDENT SIMULATION AND READINESS TESTING
PERFORMANCE METRICS AND ROI ANALYSIS
Our Certificates



i4Challenge New Ideas winner 2022/2023 by Basel Innovation Area
We are thrilled to be at the forefront of innovation, actively participating in the Basel Innovation Area.
Our involvement underscores our commitment to pioneering new technologies and contributing to success in this dynamic field.
AD HOC EMERGIENCES
- disaster recovery in ransomware & malware infections, data breaches, disrupting critical systems or services
- reverse engineering by blocking or containing the attacker & identifying the source of the attack
- successful prevention or limiting of future incidents
WHAT WE DO
PROTECTION & THREAT HUNTING
Is your network secure round the clock? Facing a data breach or incident?

WHAT WE DO
VERIFICATION & AUDITS
How do you understand your security & secured future? When did you check your cybersecurity last time?

WHAT WE DO
EDUCATION & CONSULTING
How many clients can you lose without cybersecurity compliance? How your employees can protect your company?


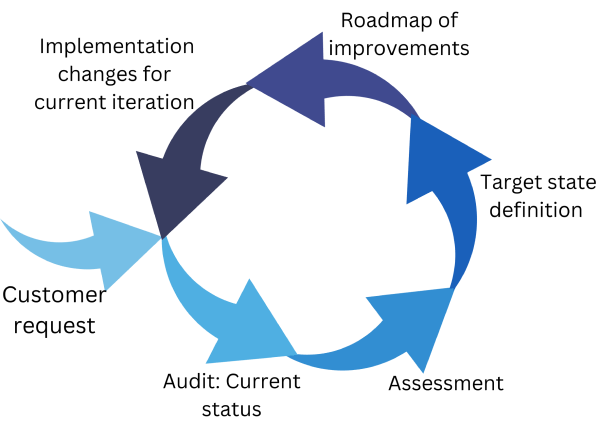
Xsight uses an iterative approach tailormade for each Customer and has highly trained professionals to construct each phase
START-UP cybersecurity level
embryonic in nature
initial capacity building
no concrete actions
FORMATIVE cybersecurity level
some aspects formulated
mainly ad-hoc
disorganized or simply new
ESTABLISHED cybersecurity level
some indicators in place
some security fields are functional
trade-off in relative investment
STRATEGIC cybersecurity level
priorities of indicators are defined according to security fields
choices conditionally reflect the organization's circumstances
DYNAMIC cybersecurity level
clear mechanisms to alter strategy depending on circumstances
rapid decision-making, reallocation of resources, and constant attention










